Many industrial IoT techniques have open doorways that create unintended vulnerabilities.
What info might be uncovered by open communications protocols? How do hackers establish weak techniques? What safety sources can be found? How do IoT firewalls defend in opposition to such threats?
TCP Port 502 vulnerabilities
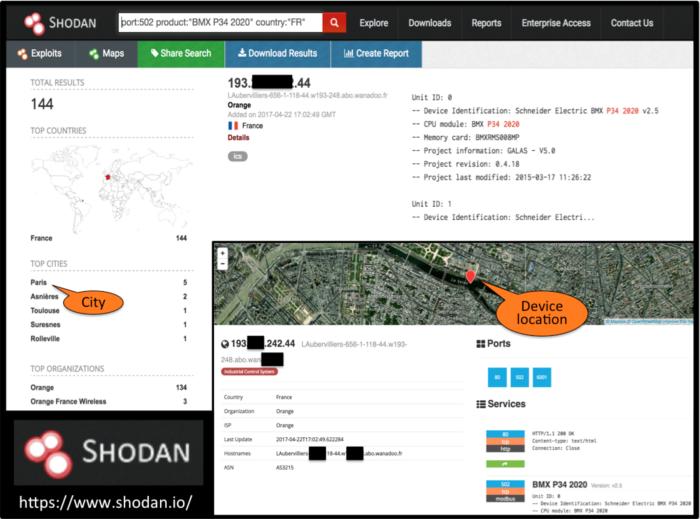
Many industrial techniques use TCP Port 502, which permits two hosts to determine a connection and trade streams of knowledge. TCP ensures supply of knowledge and that packets can be delivered on port 502 in the identical order through which they had been despatched. This creates the danger of distant attackers to put in arbitrary firmware updates through a MODBUS 125 operate code to TCP port 502. Scans from providers equivalent to Shodan establish techniques which have an open TCP port 502 that might be weak.
Security auditing corporations equivalent to Splone establish threats with scans and different penetration testing methods to suggest counter-measures. A scan returns the host’s IP handle, open ports, the nation, the seller, the product and firmware info.
xxx.xxx.xxx.xxx: Schneider Electric BMX P34 2020 /v2.5
Securing the Modbus communication protocol
Downtime is extraordinarily expensive with regards to Industrial Control Systems (ICS), HVAC gear and refrigeration techniques. Such industrial Internet of Things (IoT) techniques are particularly weak as a result of they’re deployed in a manufacturing unit however talk with exterior cloud-based IoT providers. Multiple protocols getting used and delegated administrative rights add to the safety issues.
Modbus is a serial communications protocol initially revealed by Modicon (now Schneider Electric) in 1979 to be used with its programmable logic controllers (PLCs). Simple and sturdy, it has since change into a de facto commonplace communications protocol and is now a generally out there technique of connecting industrial digital units. Modbus is extensively used and was developed with industrial purposes in thoughts. It’s straightforward to deploy and strikes uncooked bits with few restrictions.
The hazard with Modbus is that when TCP/IP packets are inspected for his or her supply IP handle, they appear innocent. What’s wanted is a deeper degree inspection. Industrial units hardly ever have a lot in the best way of application-layer safety, so extra safety is required.
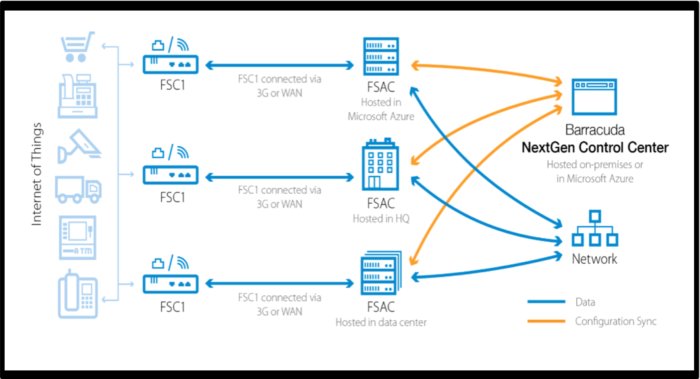
Barracuda NextGen Firewalls defend industrial IoT techniques along with different company sources. They use a small Secure Connector equipment (FSC1) to attach distant units with a number of uplinks. This additionally allows zone-based firewalling, Wi-Fi and VPN connectivity. Network site visitors is backhauled to a Concentrator (FSAC) operating at a central workplace or within the cloud the place it’s inspected for URL filtering, intrusion prevention (IPS), antivirus safety and utility detection.
The method minimizes the disruption to present techniques and offloads the safety scanning to the cloud or one other inner server. Firewall updates will be remodeled the community as new threats emerge.
Industrial IoT safety sources
- The Industrial Control Systems Cyber Emergency Response Team (ICS-CERT): ICS-CERT works to scale back dangers inside and throughout all essential infrastructure sectors by partnering with legislation enforcement companies and the intelligence neighborhood and coordinating efforts amongst federal, state, native and tribal governments and management techniques homeowners, operators and distributors. It collaborates with worldwide and personal sector Computer Emergency Response Teams (CERTs) to share management systems-related safety incidents and mitigation measures.
- The Industrial Internet Consortium has developed a Security Framework with suggestions for securing industrial IoT units that’s out there freed from cost. “To keep away from safety hazards, particularly as techniques from completely different sectors interoperate and exploitation makes an attempt are made within the gaps between them, it’s important and pressing to construct early consensus among the many members on IIoT safety,” the consortium says.
- ScadaHacker supplies safety alerts and coaching on securing Industrial IoT techniques.
Often, it simply isn’t attainable to safe all of the doorways to a constructing. A doorman that screens individuals coming out and in of the constructing can assist. For industrial IoT techniques, a doorman named Barracuda could also be simply what’s wanted.
This article is revealed as a part of the IDG Contributor Network. Want to Join?