A single submarine cable, like the one pictured provides the bulk of the nation’s internet. (Image: file photo)
One of the largest distributed denial-of-service attacks happened this week and almost nobody noticed.
Since the cyberattack on Dyn two weeks ago, the internet has been on edge, fearing another massive attack that would throw millions off the face of the web. The attack was said to be upwards of 1.1 Tbps — more than double the attack a few weeks earlier on security reporter Brian Krebs’ website, which was about 620 Gbps in size, said to be one of the largest at the time. The attack was made possible by the Mirai botnet, an open-source botnet that anyone can use, which harnesses the power of insecure Internet of Things devices.
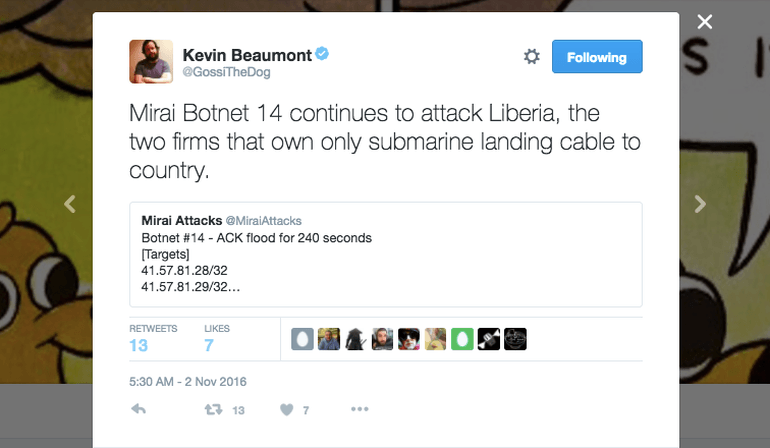
This week, another Mirai botnet, known as Botnet 14, began targeting a small, little-known African country, sending it almost entirely offline each time.
Security researcher Kevin Beaumont, who was one of the first to notice the attacks and wrote about what he found, said that the attack was one of the largest capacity botnets ever seen.
One transit provider said the attacks were over 500 Gbps in size. Beaumont said that given the volume of traffic, it “appears to be the owned by the actor which attacked Dyn.”
An attack of that size is enough to flatten even a large network — or as was seen this week, a small country.
(Image: Twitter)
The attacks were targeting Liberia, a small west African country with basic and spotty internet coverage, which has a single fiber internet cable off its shores providing internet to the country.
Just six percent of the country has an internet connection, according to official statistics. Most residents with an internet connection used satellite technology to get online until the arrival of the ACE fiber cable in 2011 along the west African coast, which provides a capacity of up to 5.1 Tbps of data, and is divided up to serve the entire coast.
Liberia — and others in the region — are particularly vulnerable to flooding attacks, because the ACE fiber cable covers the whole West African coastline, and its capacity is shared between the countries.
Botnet 14 has over the past week intermittently attacked IP addresses owned by the two Liberian companies that co-own the only fiber cable coming into the country, according to @MiraiAttacks, a Twitter tracker that monitors Mirai-based attacks.
With so few people in the country on the internet, reaching out to residents to confirm the outages wasn’t easy.
However, one Liberian resident, who returned to the country this week after months away, confirmed that their internet service suffered “minor interruptions in service” on Wednesday evening.
The outages were reported at the same time that the attacks were being carried out, according to @MiraiAttacks.
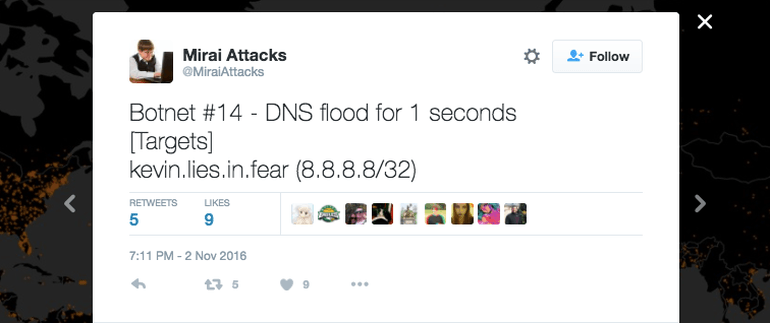
Beaumont is calling the botnet “Shadows Kill” for its subtle messages warning the security researcher off its tracks. The botnet targeted dummy sites that don’t exist, in order to be picked up by @MiraiAttacks, in an effort to send messages to Beaumont warning him off.
(Image: Twitter)
“The attacks are extremely worrying because they suggest a Mirai operator who has enough capacity to seriously impact systems in a nation state.,” said Beaumont.
Why attack Liberia? Nobody is quite sure.
One security researcher we spoke to, who didn’t want to be named for fear of reprisals, said that attacking a little-known about country might be the “best place” to test cyberweapons, like the Mirai botnet, for larger attacks.
Beaumont also thinks that the attacks “appear to be [of] a test nature.”
If a significant “test” botnet can launch an attack capable of pulling a small country’s submarine-based internet offline, that leaves open the possibility for far worse to come.

