Your IoT safety digital camera is extra doubtless to be compromised if it has a weak password.
Image: iStock
‘Admin’, ‘root’, ‘124356’, ‘password’. No marvel there was an endemic of cyberattackers hijacking Internet of Things (IoT) gadgets when default passwords are this poor and customers aren’t bothering to change them — or worse, do not have the choice to.
The variety of internet-connected gadgets has risen because the IoT has change into a better presence in houses and workplaces. However, within the rush to become involved within the development, some device producers have released products with poor security, which in flip have been breached for malicious functions together with espionage and DDoS assaults.
Arguably it was the rise of the Mirai botnet — which was comprised of IoT gadgets akin to routers and safety cameras — that lastly introduced this safety menace to public consideration. The botnet was concerned in a series of DDoS attacks that knocked some of the biggest internet services offline, together with Netflix, the PlayStation Network, and Twitter.
Embarrassingly dangerous safety
Now cybersecurity researchers at Symantec have revealed the commonest passwords used on IoT gadgets are sometimes weak, and thus prone to hackers. Researchers arrange an IoT honeypot — which seems on searches as an open router — to observe assaults in opposition to IoT gadgets. The commonest passwords utilized by attackers to achieve brute-force entry present that many programs lack even rudimentary security.
The prime ten passwords used to entry the honeypot are detailed in Syamtec’s Internet Security Threat Report for 2017. The commonest is solely ‘admin’, accounting for 36.5 % of all logins, whereas ‘root’ is used for an extra 16 %.
Next, ‘1234’, ‘12345’, and ‘123456’ account for a few quarter of assaults on the honeypot, whereas ‘password’ additionally ranks amongst probably the most generally used passwords to entry gadgets.
The default password for the Ubiquiti model of routers, ‘ubnt’ options within the prime ten, doubtless because routers were targeted following the revelation that an old vulnerability hadn’t been patched.
Other weak passwords used to breach IoT gadgets embrace ‘check’, ‘admin123’, and ‘abc123’.
Why achieve this many gadgets have such poor passwords?
First, customers won’t have any concept how to change them, Symantec suggests. And second, distributors are hard-coding usernames and passwords into gadgets with out giving customers the power to change them.
“There are so many devices with poor security of default credentials, it just makes it so easy to launch massive scanning efforts and automatically add vulnerable devices to your botnet and use that as DDoS service for hire,” Symantec researcher Dick O’Brien informed ZDNet.
“You can’t have hard-coded credentials in devices like that; you need to be able to make it apparent that the end user has to change the password on it,” he mentioned. “Hopefully greater awareness is going to seep into the market in the coming year.”
Attacks on the rise
Greater safety of IoT gadgets goes to be wanted as an increasing number of device enter the market, offering much more targets for cybercriminals.
Cyberattacks on Symantec’s honeypot nearly doubled from January to December final 12 months. An common of four.6 distinctive IP addresses hit the honeypot each hour in January, rising to eight.eight in December, with an assault going down each two minutes throughout peak instances, akin to when Mirai was increasing.
The menace of insecure IoT gadgets is a world drawback too, with contaminated gadgets concentrating on the honeypot from throughout the globe. China accounted for over 1 / 4 of IoT-based assaults, adopted by the United States, Russia, and Europe.
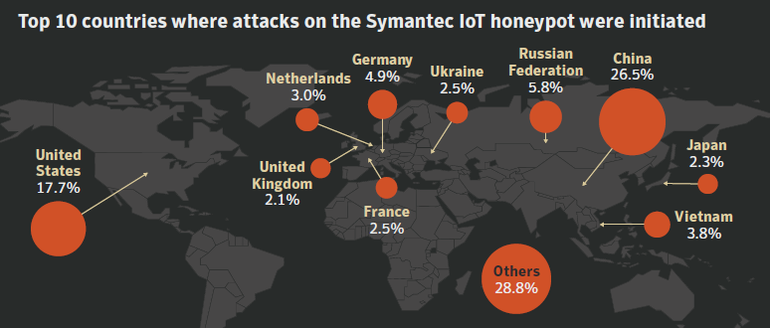
China and the United States had been the main areas for IoT assaults.
Image: Symantec
These metrics measure the nations through which the IP tackle of the attacking device was based mostly. However, that does not essentially imply the attackers themselves had been based mostly in these nations.
With billions more devices set to be connected to the internet by 2020, extra should be finished to make sure the safety of IoT. “Currently, the poor security on IoT devices is just making life easier for cyber criminals,” Symantec warns.








