A brand new variety of assault is concentrating on unsecured Internet of Things gadgets by scrambling their code and rendering them ineffective.
Security agency Radware first spotted the newly-found “BrickerBot” malware final month after it began hitting its personal honeypots, logging a whole lot of an infection makes an attempt over a number of days. When the malware connects to a tool with their default usernames and passwords — usually simply discovered on the web — the malware corrupts the system’s storage, resulting in a state of everlasting denial-of-service (PDoS) assault, referred to as “bricking.”
In different phrases, this assault, “damages a system so badly that it requires replacement or reinstallation of hardware,” mentioned Radware.
It’s a novel tackle an ongoing safety downside with Internet of Things gadgets: botnets managed by hackers, just like the Mirai malware, sometimes infect unsecured gadgets that are enlisted as half of wider bandwidth-stealing assaults to convey down web sites and companies by overwhelming them with web visitors.
Like the Mirai botnet, most well-known for bringing down wide swathes of the US internet final yr in a large distributed denial-of-service (DDoS) assault, the BrickerBot additionally makes use of “the same exploit vector” by brute-forcing telnet accounts with lists of out there usernames and passwords.
Radware would not have an inventory of internet-connected gadgets, like webcams, toys, and even sensible bulbs, in danger of being attacked, however pointed to a number of varieties of Linux-based gadgets that run the BusyBox toolkit that have their telnet port open, and are uncovered publicly on the web.
The researchers say that the attackers even have an affinity for concentrating on gadgets on Ubiquiti networks, which have been targeted by attackers earlier than.
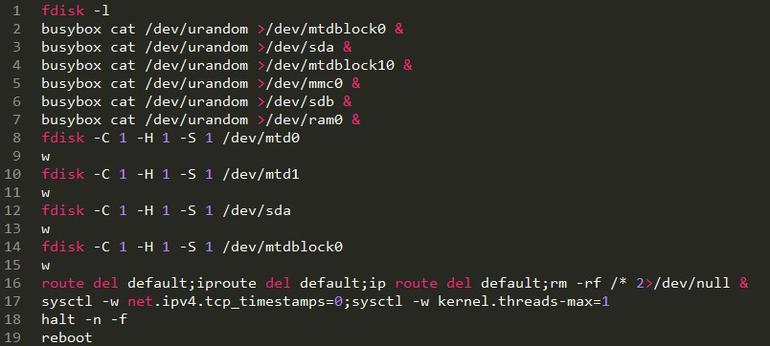
Once inside, the malware runs a sequence of instructions, which “try to remove the default gateway, wipe the device through rm -rf /* and disable TCP timestamps as well as limiting the max number of kernel threads to one,” which might scramble the system’s reminiscence.
The researchers additionally say that the malware provides further instructions “to flush all iptables firewall and NAT rules and add a rule to drop all outgoing packets,” successfully wiping any hint of its an infection.
“Unfortunately, even after performing the factory reset, the camera was not recovered and hence it was effectively bricked,” mentioned Radware.
(Image: Radware)
And, as a result of the device-bricking bot conceals its location via the Tor anonymity community, there is no option to know the place the assault got here from, the researchers mentioned.
The emergence of BrickerBot has prompted Homeland Security’s Cyber Emergency Response Team (CERT) to concern an updated warning, noting that “no information is available at this time about the type and number of devices used in performing these attacks.”
“Control systems often have Internet accessible devices installed without the owner’s knowledge, putting those systems at increased risk of attack,” mentioned the advisory.
The researchers say that a tool search might level to a minimum of 21 million gadgets in danger, however the motivations for this new assault aren’t recognized.
Homeland Security suggests altering a tool’s default credentials and disabling telnet.
