This is Part Two of PCMag’s three-part trend overview breaking down the enterprise Internet of Things landscape through the lens of this year’s Mobile World Congress. Check out Part One on enterprise use cases here.
You can’t talk about enterprise-ready IoT without addressing the botnet-sized security elephant in the room. The historic, global scale of the Mirai botnet DDoS attack put a much-needed spotlight on IoT security and it goes far beyond changing default passwords. Part Two of our MWC series on IoT and business dissects how manufacturers and security providers are approaching the complex proposition of IoT security on a number of different levels.
 There’s a laundry list of factors for businesses to consider in IoT security: data integrity and privacy, chip and firmware security features, app- and device-level encryption, and much more. When it comes to the notoriously attack-prone smart home and consumer-facing smart devices, PCMag’s Max Eddy’s recent feature has you covered on why those devices are so vulnerable. He also explains how endpoint security providers as well as manufacturers such as Philips are securing them.
There’s a laundry list of factors for businesses to consider in IoT security: data integrity and privacy, chip and firmware security features, app- and device-level encryption, and much more. When it comes to the notoriously attack-prone smart home and consumer-facing smart devices, PCMag’s Max Eddy’s recent feature has you covered on why those devices are so vulnerable. He also explains how endpoint security providers as well as manufacturers such as Philips are securing them.
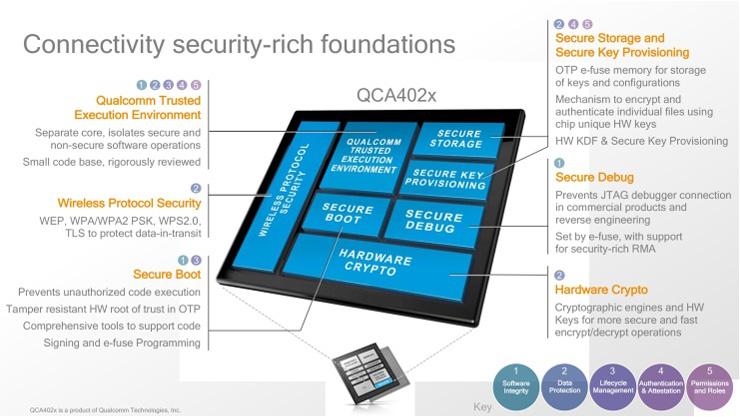
From an enterprise perspective, it’s about a bottom-up view of IoT security that secures every level along the way. At the chip level, Qualcomm’s Talluri explained how the company is working to extend its smartphone security architecture to IoT devices.
“When we first started working on phones, we did a lot of work inside the chip. Hardware security, secure boot, device authentication, bitstream security—all these things we built into the chips,” said Talluri. “We’re working to take that and put it into IoT processors for making things like Wi-Fi chips. We’re putting a lot into hardware-based security in these IoT chipsets.”
IoT Security: A Layer-by-Layer Approach
The most difficult aspect of the IoT security proposition is the ability to bake it in throughout the manufacturing process. Richard Parris is the CEO of cybersecurity and identity management company Intercede. The company works with enterprises, governments, and manufacturers (including ARM and Intel) on device security and cryptographic key management. Parris framed IoT security in the context of the manufacturing pipeline.
“To ensure IoT security, you have to go into the ecosystem at the right place,” said Parris. “You can only solve the problem of IoT trust if it’s baked into the silicon at the point of manufacture. You need silicon that’s secure by design. In fact, all the major silicon manufacturers have been building in the necessary capabilities for several years. ARM has a technology called TrustZone that goes back more than a decade. Intel does it. Imagination Technologies has Omni Shield. Big manufacturers take the capability from the baseline IP designer when they go through foundries and put additional OS capabilities atop the silicon.”
Parris explained that, while chip manufacturers are all enabling rich security capabilities, what hasn’t happened is the emergence of an easy means by which IoT device manufacturers can switch those features on. That’s why Intercede, along with ARM, Solacia, and Symantec, recently released the Open Trust Protocol (OTrP), an open architecture and framework for IoT device management and data integrity. (We get into how it works in Part Three of this feature.)
That’s the next step in layering in comprehensive IoT security. Device makers need to marry built-in chip security with app- and device-level features for end-to-end protection. Global design and engineering firm Aricent works to do just that for enterprises.
Walid Negm, CTO, and Prakasha Ramchandra, Executive Vice President of Technology and Innovation, explained how Aricent approaches holistic IoT security. The company works with clients across a number of industries, including semiconductors, industrial clients, enterprise and consumer software companies, telecommunications, and online or cloud-based service companies. In some way, shape, or form, all of the companies plug into the IoT ecosystem.
“When you try to unpack what IoT security actually is, the easiest way is to pick an endpoint. All the data from that endpoint is moving over to a network and then backhauled wirelessly to a data center,” said Negm. “And you need the scale to support millions and millions of endpoints. We work on endpoints as well as how you manage the infrastructure. You have to think about not just the endpoint but the relationship between the human interacting with Alexa, for example. You have to think about identity management: how you establish you’re the owner of the device and how you share that information.”

Aricent has a solution called Converged IoT, which stitches together IoT security on a number of fronts to do the heavy lifting for enterprises. Aricent builds a custom security profile for IoT devices by combining cloud-connected endpoints, device-level management, and an array of drivers, sensors, and reporting data embedded within the IoT hardware. As Ramachandra explained, the company aims to homogenize IoT security across industries by taking silicon and hardware platforms and packaging them up with a security profile as part of an orchestration framework that accelerates time-to-market.
“Converged IoT starts with a smart endpoint that has hybrid components like a Snapdragon 1100 [wearable processor] and additional sensors within the device-client architecture,” explained Ramchandra. “Qualcomm provides the basic Linux OS. And we’ve added additional driver connectivity and reporting on the sensor data going back to the cloud through Bluetooth. We then package that into a security profile.”
“Part of the value proposition is to do some of that heavy lifting ahead of time with these IoT reference designs because our clients are competing on speed,” Ramchandra added. “They’re trying to navigate these fast-moving forces to bring products to market faster and bring intelligence to the customer experience. We provide a product framework with things like threat intelligence, static and dynamic code analysis, vulnerability and penetration testing, and cryptography recommendations to keep traffic secure in transit while making sure products are still developed in an agile manner.”
Frameworks and security profiles aren’t Aricent’s only tools for enabling and enforcing enterprise-grade IoT security. Aricent, along with several other companies I spoke to at MWC, are also experimenting with blockchain as an underlying fabric to tie the IoT ecosystem securely together.
For more on that, as well as for a breakdown of the current standardization efforts around IoT interoperability, head to Part Three of this story.