A new Internet of Things (IoT) botnet is focused over 1,000 totally different fashions vulnerable of IP cameras and utilizing the hijacked units to perform DDoS assaults.
Over 122,000 cameras from quite a lot of producers are vulnerable to changing into a part of the Persirai botnet – and the overwhelming majority of homeowners do not even know their units are uncovered on the web and thus simply focused by malware.
Discovered by cybersecurity researchers at Trend Micro 122,069 of the affected IP cameras throughout the globe can simply be found through the Shodan IoT search engine– with vulnerable merchandise seen in China and Japan, by Europe and all the way in which throughout to the Americas.
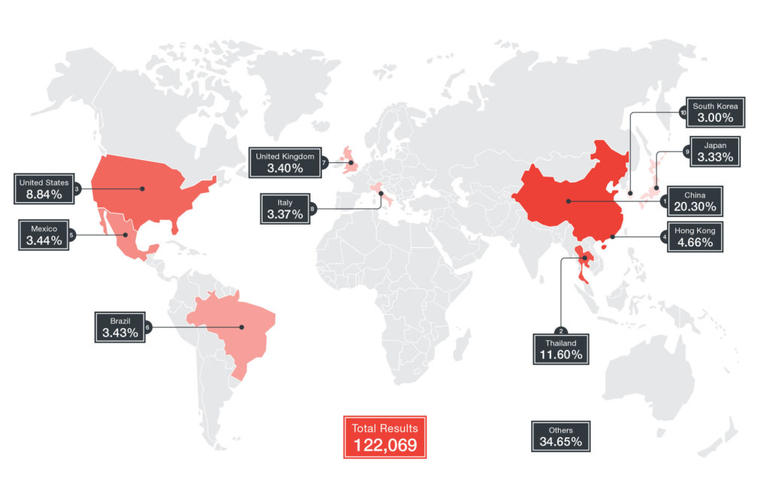
Distribution of units vulnerable to Persirai
Image: Trend Micro
Like many internet connected devices, these cameras are constructed to be simply arrange by the person – a design characteristic which regularly ends in cybersecurity being an afterthought. As a results of this, the IP cameras can open a port on the router and act like a server, making them extremely seen to IoT malware.
Taking benefit of this, the attackers are in a position to entry the IP digicam by the open port then merely carry out a command injection to power the digicam to join to a obtain website which can execute a malicious script shell and set up malware onto the digicam, roping it into the botnet.
Once downloaded and executed, the malware will delete itself and can solely run in reminiscence in an effort to keep away from detection. Persirai’s builders additionally take the step of blocking the exploit they use so as to stop different attackers from concentrating on the digicam and hold the contaminated gadget to themselves.
The cameras may be instructed to perform DDoS assaults in opposition to goal networks – an assault which whereas unsophisticated has the potential to do large injury – as demonstrated by the Mirai botnet attacks last year, which resulted in bringing giant swathes of the web and on-line providers to a standstill.
While researchers have been unable to particularly establish these behind this IoT malware, the C&C servers have been traced to Iran and the creator of the malware used some particular Persian characters within the code.
Internet of Things gadget stay vulnerable to cyberattacks as many producers rush out units with out correct safety measures and ship them to shoppers who’re unlikely to understand how to change the default credentials, leaving devices open to attack.
The unhealthy information is the safety worries across the IoT are solely doubtless to worsen as more and more devices become connected, offering cybercriminals and hackers with billions extra units to breach.
These not solely present them with the chance to perform DDoS assaults, a vulnerable IoT gadget could provide a gateway onto a network as a whole, permitting hackers to perform different legal duties together with espionage on course organisations.